Key Takeaways
- Next-generation firewalls (NGFWs) provide advanced inspection and control to secure modern networks.
- Best practices—from clear policy definitions to threat intelligence updates—ensure the long-term effectiveness of firewalls.
- Adopting emerging technologies, including AI and Zero Trust, is crucial for maintaining a future-ready security posture.
Table of Contents
- Essential Features of Next-Generation Firewalls
- Best Practices for Firewall Implementation
- Emerging Technologies in Firewall Security
- Conclusion
In an era marked by increasingly sophisticated cyber threats and rapidly changing digital environments, organizations need robust defenses to secure their infrastructures. One of the most proactive steps is deploying a modern firewall that not only meets today’s security demands but is also adaptable to tomorrow’s threats. As businesses transition to hybrid and cloud-first models, adopting next-generation firewall solutions is crucial for comprehensive protection. Understanding what sets future-ready firewalls apart is essential for establishing a robust cybersecurity foundation.
Future-ready firewalls provide advanced capabilities, rapid threat detection, and consistent protection across both on-premises and cloud environments. Deploying the right firewall solution enables organizations to strengthen breach prevention, reduce risk exposure, and remain resilient as attack methods continue to evolve. Modern platforms leverage automation, artificial intelligence, and tight integration with broader security ecosystems, enabling IT teams to respond more quickly and effectively to complex threats. Solutions such as Versa Networks’ Next-Generation Firewall, detailed at https://versa-networks.com/products/next-generation-firewall/, exemplify how unified security and intelligent policy enforcement can help organizations stay ahead of increasingly sophisticated cyber adversaries.
As new security frameworks, such as Zero Trust and automated threat intelligence, become the backbone of digital security, understanding which firewall features and best practices are most critical will help your organization remain agile. Staying current with emerging firewall technologies and their integrations is vital—not just for compliance, but to safeguard reputation and business continuity.
A careful approach to configuration and proactive management, combined with a commitment to periodic review and the adoption of new technologies, will position any business to handle threats now and in the future effectively. For broader context on evolving cybersecurity threats and prevention strategies, refer to expert insights at CSO Online.
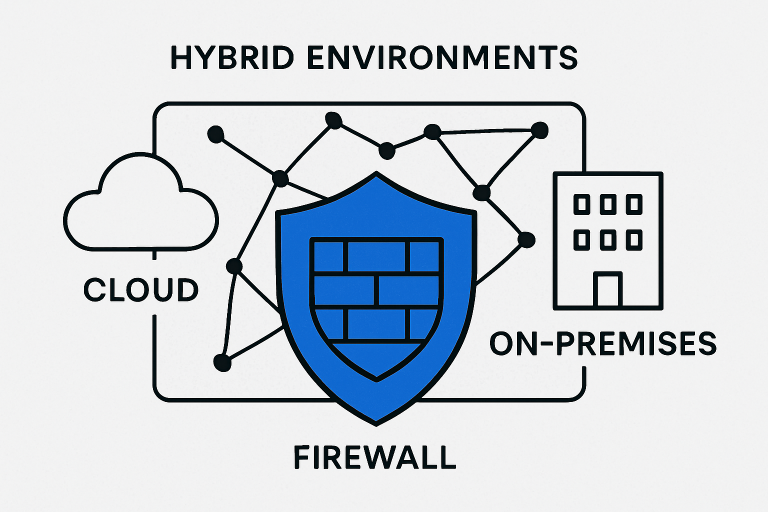
Essential Features of Next-Generation Firewalls
To truly achieve future-ready status, a firewall must provide more than traditional perimeter defense. Essential features empower organizations to monitor, inspect, and adapt to the full scope of today’s multi-layered threats:
- Deep Packet Inspection (DPI): This advanced capability doesn’t just check packet headers; it analyzes the entire content, identifying and blocking malware and unauthorized exfiltration even if it’s hidden inside seemingly normal network traffic.
- Integrated Intrusion Prevention Systems (IPS): Combining IPS with firewall functions increases your chance of detecting suspicious behavior, vulnerabilities, and active threats—stopping potential breaches before they escalate.
- Application Awareness and Control: Application-level filtering and management ensure only safe and necessary programs access your network. This limits potential attack surfaces arising from shadow IT or outdated applications.
- SSL/TLS Decryption: As more traffic becomes encrypted, examining these flows for threats is critical. Decrypting and inspecting secured data ensures attackers can’t exploit encrypted channels as a blind spot in your security posture.
- Cloud Integration: Unified control across on-premises and cloud environments is non-negotiable for businesses adopting hybrid or multi-cloud architectures. Effective integration maintains consistent policy application and visibility, regardless of where applications and data reside.
Real-World Advantages
Implementing these features isn’t just about technical capability—it’s about real-world results. Organizations equipped with DPI and application awareness reduce the risk of sophisticated attacks, such as ransomware and data theft. Cloud integrations unlock scalability and visibility, which are crucial for modern IT teams, making the firewall a critical asset in the broader security ecosystem. For examples of how layered defenses strengthen overall resilience, visit CSO Online.
Best Practices for Firewall Implementation
Even the most advanced firewall can’t guarantee robust security unless it’s paired with strong practices and ongoing management. Here are the top best practices to maximize your investment:
- Define Clear Security Policies: Develop precise, risk-aligned rules for permitted applications, services, and users. Clearly articulated policies eliminate guesswork, ensuring consistent enforcement and minimizing the likelihood of human error.
- Regularly Update Threat Intelligence: IoCs (Indicators of Compromise) and exploits change constantly. Keep your firewall informed with fresh threat intelligence feeds from trusted suppliers to recognize and block emerging threats.
- Conduct Periodic Security Assessments: Regular reviews help uncover vulnerabilities caused by misconfiguration, outdated rules, or new business demands. Frequent audits help adapt security as your network evolves.
- Implement Zero Trust Architecture (ZTA): Assume every attempt to access a resource could be malicious—enforce continuous authentication and authorization for every user, device, and application across the network.
- Utilize AI and Machine Learning: Automating detection and response through AI/ML technologies enables organizations to swiftly adapt policies and identify abnormal behaviors, thereby reducing manual intervention and the window of exposure.
Emerging Technologies in Firewall Security
The pace of innovation in cybersecurity means today’s leading solutions quickly become tomorrow’s baseline. Three main technologies are shaping the next generation of firewall protection:
- AI-Driven Firewalls: Leveraging artificial intelligence, these firewalls monitor network traffic patterns at scale, autonomously blocking malicious activity and improving as new threats emerge. Adaptive learning ensures security remains proactive, not just reactive.
- Hybrid Mesh Firewalls: These provide unified, context-aware protection across physical, virtual, and cloud environments—essential for organizations with multiple infrastructure types.
- Integration with Zero Trust Ecosystems: Firewalls natively tied into Zero Trust architectures bring granular identity verification to the forefront, strengthening defenses against lateral threat movement and insider risk.
Conclusion
As cyber threats continue to grow in sophistication and reach, traditional network defenses are increasingly challenged to keep pace. Future-ready firewalls address this gap by providing advanced capabilities such as deep packet inspection, real-time threat intelligence, and seamless protection across cloud, on-premises, and hybrid environments. These technologies enable organizations to detect and respond to attacks more effectively before damage occurs. When paired with strong security policies, employee awareness, and continuous monitoring, they form a resilient defense strategy. By evolving security controls, partnering with trusted technology providers, and closely tracking emerging threats, organizations can maintain compliance while proactively protecting critical systems, sensitive data, and brand reputation in an ever-changing digital landscape.